Google Cloud Private Service Connect and Snowflake¶
This topic describes concepts and how to configure Google Cloud Private Service Connect to connect your Google Cloud Virtual Private Cloud (VPC) network subnet to your Snowflake account hosted on Google Cloud without traversing the public Internet.
Note that Google Cloud Private Service Connect is not a service provided by Snowflake. It is a Google service that Snowflake enables for use with your Snowflake account.
Overview¶
Google Cloud Private Service Connect provides private connectivity to Snowflake by ensuring that access to Snowflake is through a private IP address. Snowflake appears as a resource in your network (that is, customer network), but the traffic flows one-way from your VPC to Snowflake VPC over the Google networking backbone. This setup significantly simplifies the network configuration while providing secure and private communication.
The following diagram summarizes the Google Cloud Private Service Connect architecture with respect to the customer Google Cloud VPC and the Snowflake service.
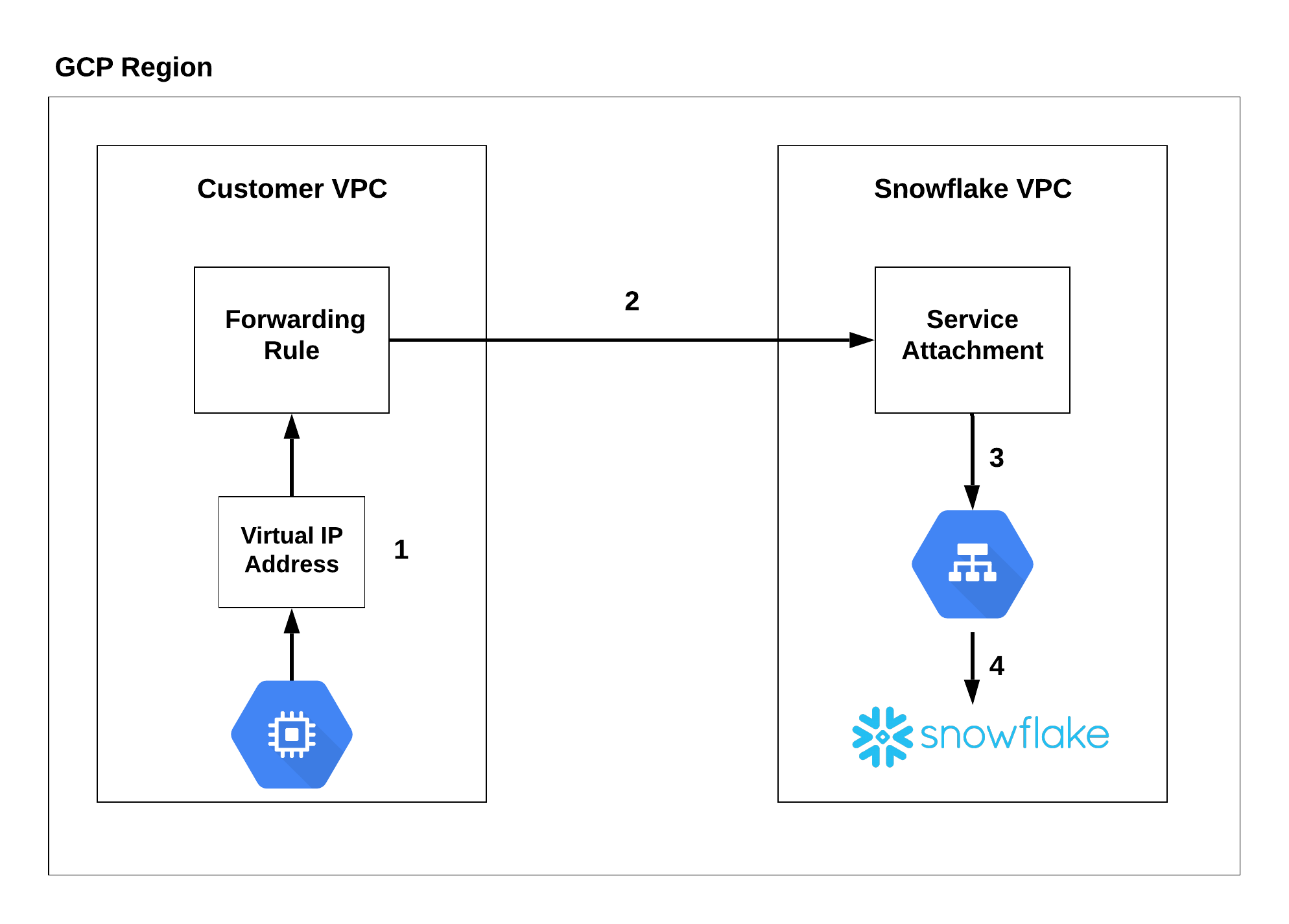
The Google Compute Engine (that is, a virtual machine) connects to a private, virtual IP address that routes to a forwarding rule (1). The forwarding rule connects to the service attachment through a private connection (2). The connection is routed through a load balancer (3) that redirects to Snowflake (4).
Limitations¶
Maximum 10 connections per project.
Maximum 50 connections per account.
Some Snowflake system functions for self-service management are not supported. For information, see Current Limitations for Accounts on Google Cloud.
For details, see:
Configure your Google Cloud VPC environment¶
This section covers the Snowflake-specific details for configuring your Google Cloud VPC environment.
Important
Snowflake is not responsible for the configuration of your Google Cloud environment. This procedure shows the basics of using the Google Cloud CLI, but is not a definitive guide. For example:
You could use the Google Cloud console to configure your Google Cloud environment instead of the Google Cloud CLI, which would change the steps. For example, when using the Google Cloud console, you are creating an endpoint, not a forwarding rule.
It does not show you how to configure required firewall updates and DNS records.
It does not show you how to make an endpoint available in other regions (Private Service Connect endpoints are regional resources). For more information about making an endpoint available in other regions, see the Google documentation.
For additional help, contact your internal Google Cloud administrator.
As a Snowflake account administrator (that is, a user with the ACCOUNTADMIN system role), open a worksheet and call the SYSTEM$GET_PRIVATELINK_CONFIG function. You need to save the output for subsequent steps.
For example:
USE ROLE ACCOUNTADMIN; SELECT key, value FROM TABLE(flatten(input=>parse_json(system$get_privatelink_config())));
Use the Google Cloud CLI to update the gcloud library to the latest version:
gcloud components update
Authenticate to Google Cloud using the following command:
gcloud auth login
In your Google Cloud VPC, set the project ID in which the forwarding rule should reside.
gcloud config set project <project_id>
To obtain a list of project IDs, execute the following command:
gcloud projects list --sort-by=projectId
In your Google Cloud VPC, create a virtual IP address:
gcloud compute addresses create <customer_vip_name> \ --subnet=<subnet_name> \ --addresses=<customer_vip_address> --region=<region>
Where:
customer_vip_namespecifies the name of the virtual IP rule (for example,psc-vip-1).subnet_namespecifies the name of the subnet.customer_vip_addressspecifies an IP address to which all private connectivity URLs resolve. Specify an IP address from your network or use CIDR notation to specify a range of IP addresses.regionspecifies the cloud region where your Snowflake account is located.
For example:
gcloud compute addresses create psc-vip-1 \ --subnet=psc-subnet \ --addresses=192.168.3.3 \ --region=us-central1
Output:
Created [https://www.googleapis.com/compute/v1/projects/docstest-123456/regions/us-central1/addresses/psc-vip-1].Create a forwarding rule to have your subnet route to the Private Service Connect endpoint, and then to the Snowflake service endpoint.
gcloud compute forwarding-rules create <name> \ --region=<region> \ --network=<network_name> \ --address=<customer_vip_name> \ --target-service-attachment=<privatelink-gcp-service-attachment>
Where:
namespecifies the name of the forwarding rule.regionspecifies the cloud region where your Snowflake account is located.network_namespecifies the name of the network for this forwarding rule.customer_vip_namespecifies the<name>value (that is,psc-vip-1) of the virtual IP address created in the previous step.privatelink-gcp-service-attachmentspecifies the endpoint for the Snowflake service, which you obtained when you executed the SYSTEM$GET_PRIVATELINK_CONFIG function in an earlier step.
For example:
gcloud compute forwarding-rules create test-psc-rule \ --region=us-central1 \ --network=psc-vpc \ --address=psc-vip-1 \ --target-service-attachment=projects/us-central1-deployment1-c8cc/regions/us-central1/serviceAttachments/snowflake-us-central1-psc
Output:
Created [https://www.googleapis.com/compute/projects/mdlearning-293607/regions/us-central1/forwardingRules/test-psc-rule].Use the following command to verify the forwarding-rule was created successfully:
gcloud compute forwarding-rules list --regions=<region>
Where:
regionis the cloud region where your Snowflake account is located. For example, if your Snowflake account is located in theeurope-west2region, replace<region>witheurope-west2.
For a complete list of Google Cloud regions and their formatting, see Viewing a list of available regions.
Update your DNS settings.
All requests to Snowflake need to be routed through the Private Service Connect endpoint so that the URLs returned by the SYSTEM$GET_PRIVATELINK_CONFIG function resolve to the VIP address that you created (
<customer_vip_address>).The values to obtain from the output of SYSTEM$GET_PRIVATELINK_CONFIG depend on which Snowflake features you access using private connectivity. For a description of the possible values, see Return values.
Note that the values for
regionless-snowsight-privatelink-urlandsnowsight-privatelink-urlallow access to Snowsight and the Snowflake Marketplace using private connectivity. However, there is additional configuration if you want to enable URL redirects. For information, see Snowsight & Private Connectivity.Note
A full explanation of DNS configuration is beyond the scope of this procedure. For example, you can choose to integrate a private DNS zone into your environment using Cloud DNS. Please consult your internal Google Cloud and cloud infrastructure administrators to configure and resolve the URLs in DNS properly.
Connect to Snowflake¶
Before connecting to Snowflake, you can optionally leverage SnowCD (Snowflake Connectivity Diagnostic tool) to evaluate the network connection with Snowflake and Private Service Connect. For more information, see SnowCD and SYSTEM$ALLOWLIST_PRIVATELINK.
To connect to Snowflake with your private connectivity account, see Connecting with a URL.
Using SSO with Google Private Service Connect¶
Snowflake supports using SSO with Google Cloud Private Service Connect. For more information, see:
Using Client Redirect with Google Cloud Private Service Connect¶
Snowflake supports using Client Redirect with Google Cloud Private Service Connect.
For more information, see Redirecting client connections.
Using Replication & Tri-Secret Secure with Private Connectivity¶
Snowflake supports replicating your data from the source account to the target account, regardless of whether you enable Tri-Secret Secure or this feature in the target account.
Blocking public access — Recommended¶
After testing the Google Cloud Private Service Connect connectivity with Snowflake, you can optionally block public access to Snowflake using network policies. For more information, see Controlling network traffic with network policies.
Configure the CIDR block range to block public access to Snowflake using your organization’s IP address range. This range can be from within your virtual network.
Once the CIDR Block ranges are set, only IP addresses within the CIDR block range can access Snowflake.
To block public access using a network policy:
Create an IPv4 network rule or edit an existing IPv4 network rule to add the CIDR block range for your organization.
Create or modify a network policy to use the IPv4 network rule.
Activate the network policy for your account.