Pinning private connectivity endpoints for inbound traffic¶
For Snowflake accounts on Amazon Web Services (AWS) and Microsoft Azure (Azure), you can pin (specify, register, and map) private connectivity endpoints to your account. By pinning private endpoints to your account, Snowflake ensures that the inbound traffic originating from the pinned endpoints only goes to the account that pinned them. Snowflake recommends using pinned endpoints, network policies, and network rules to harden your security posture by reducing the network attack surface to your Snowflake account.
Tip
Pinning allows only authorized private endpoint(s) to be used to send traffic from the customer network to a specific Snowflake account. If you want to restrict inbound access to Snowflake accounts from specific lists of IPs and VPCE IDs/LinkIDs, use network policies and network rules.
Snowflake enforces a private endpoint pinning check at the point of ingress for every request received over private connectivity. This check compares two key pieces of information:
The endpoint ID provided in the request header.
The account that pinned the endpoint, as recorded in Snowflake’s metadata.
If these match — in other words, if the request originates from the account that registered the endpoint — then Snowflake allows the connection. Otherwise, Snowflake blocks the connection.
For example:
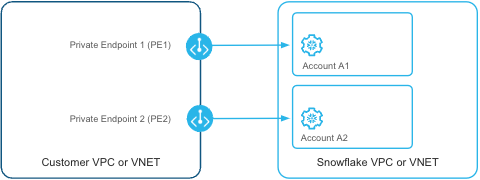
Pinned private endpoint |
Snowflake account that pinned private endpoint |
Request’s target Snowflake account |
Snowflake pinning check decision |
|---|---|---|---|
PE1 |
A1 |
A1 |
ALLOW |
PE1 |
A1 |
A2 |
DENY |
PE2 |
A2 |
A1 |
DENY |
PE2 |
A2 |
A2 |
ALLOW |
Prerequisites¶
Before pinning a private endpoint, you must:
Configure a private link for your Snowflake account on AWS or Azure.
Limit the scope of the access token you use to register an endpoint with your Snowflake account.
For more information about configuring private links, see AWS PrivateLink or Azure Private Link.
Important
Before you pin a private endpoint, when Configuring private connectivity for Snowsight, ensure that the endpoint uses a regionless Snowsight privatelink URL for all your accounts. A regional Snowsight privatelink URL will not connect to a pinned private endpoint.
Manage enforcement with the delay time argument¶
After configuring your private links, you call the SYSTEM$REGISTER_PRIVATELINK_ENDPOINT system function to register a private connectivity endpoint with your Snowflake account. In that function call, you can optionally specify a delay time. The delay time is the number of minutes to wait before enforcing the private endpoint registration. The delay time value helps prevent you from accidentally blocking yourself from accessing Snowflake when you register a new private endpoint. The maximum delay time is 1440 minutes (24 hours) and the default value is 60 minutes.
The private endpoint that you register for your Snowflake account can also be registered for other Snowflake accounts. For example, you might have three Snowflake accounts and you want to ensure that the connection to each Snowflake account only goes through one registered private endpoint. By setting the delay time argument to 60 minutes, you allow for sufficient time to register the private connectivity endpoint with each Snowflake account.
However, when you register a private connectivity endpoint and specify a delay time, you must be mindful of the local timestamp of the first account in which you call the system function. The enforcement time is based on the local timestamp of the first account when you call the system function plus any delay time that you specify, relative to a specific private connectivity endpoint.
For example, consider pinning a single private connectivity endpoint with three accounts in the same time zone:
If you call the system function in
account1at 10:00 AM and specify a delay time of 60 minutes, the enforcement time is 11:00 AM.If you call the system function in
account2at 10:30 AM, the enforcement time is 11:00 AM.If you call the system function in
account3at 11:01 AM, the enforcement time is immediate (now).
Tip
Store the timestamp of when you register the private endpoint in the first account. Maintain a record of the accounts that are pinned to a particular private endpoint.
If you anticipate registering multiple accounts and a delay time of 1440 minutes is not enough time, contact Snowflake Support.
Managing access token scope on Microsoft Azure¶
Before pinning a private endpoint to your Snowflake account on Azure, you must limit the scope of the access token that you pass into the SYSTEM$REGISTER_PRIVATELINK_ENDPOINT system function. Requiring the caller to scope the access token to the private endpoint helps Snowflake authorize the caller’s access to the endpoint. This means that the token is only valid for the private endpoint and the Snowflake account where you call the system function.
Important
Do not use the token used in the SYSTEM$AUTHORIZE_PRIVATELINK system function. The following steps generate a token unique to SYSTEM$REGISTER_PRIVATELINK_ENDPOINT.
To limit the scope of the access token for your private endpoint on Azure, do the following steps in your Microsoft Azure account:
Create a subscription custom role definition for a role called
snowflake-pep-role, and replace thesubscription_idplaceholder with the ID of your subscription.The subscription ID must match the subscription where the private endpoint exists. You only need to create the role definition once for your subscription.
Create the role assignment and assign the
snowflake-pep-rolerole and private endpoint scope to a user (or a group). Replace the placeholders for theuserand theprivate_endpoint_resource_id.Generate the access token to use with the SYSTEM$REGISTER_PRIVATELINK_ENDPOINT system function. Replace the
subscription_idplaceholder with the ID of your subscription.
Managing access token scope on Amazon Web Services¶
Before pinning a private endpoint to your Snowflake account on AWS, you must limit the scope of the access token that you pass into the SYSTEM$REGISTER_PRIVATELINK_ENDPOINT system function. Requiring the caller to scope the access token to the private endpoint helps Snowflake authorize the caller’s access to the endpoint. This means that the token is only valid for the private endpoint and the Snowflake account where you call the system function.
Important
Do not use the token used in the SYSTEM$AUTHORIZE_PRIVATELINK system function. The following steps generate a token unique to SYSTEM$REGISTER_PRIVATELINK_ENDPOINT.
To limit the scope of the access token for your private endpoint on AWS, generate a federated token, as shown in the following example:
Example¶
As a representative example, register an endpoint to route your connection to the Snowflake service.
Configure AWS PrivateLink or Azure Private Link for your Snowflake account. If you already have this service configured, skip to the next step.
Log in to Snowflake by using the public internet, and use the URL that doesn’t contain a
privatelinksegment in the URL.Call the SYSTEM$REGISTER_PRIVATELINK_ENDPOINT system function to register the VPC endpoint with your Snowflake account. The
tokenarguments contain truncated values and the delay time unit is minutes:AWS
Azure
To confirm the private connectivity endpoint mapping, call the SYSTEM$GET_PRIVATELINK_ENDPOINT_REGISTRATIONS system function.
You can unregister the private connectivity endpoint from your Snowflake account by calling the SYSTEM$UNREGISTER_PRIVATELINK_ENDPOINT system function.
Important
If you register a VPC endpoint or private endpoint in Snowflake and delete the endpoint in your VPC or VNet, you must call the SYSTEM$UNREGISTER_PRIVATELINK_ENDPOINT system function in your Snowflake account to unregister the endpoint. Otherwise, your connection to the Snowflake Service can’t use private connectivity. It uses the public internet.